EvotecIT
Security Services
Boost Your Success
EvotecIT provides industry leading solutions, combined with expert design, installation and support, to empower your business to succeed and remain secure.
Protect company information through constantly changing security processes.
Reduce risk of data loss and malware infection..
Be ready with server backup and site recovery by connecting clouds.
Enable high speed internet access across the network.
Actively Managed Systems
We know that the needs of our customers are going to vary, that is why we provide customised support solutions to meet each of our customers requirements. From the day-to-day essentials such as emails to comprehensive cloud solutions, we ensure we thoroughly assess our customers requirements and provide the right solutions and services. We offer a wide range of IT services including setup, installation, repairs, upgrades, virus & malware removal, troubleshooting, backup, disaster recovery, as well as migration to Cloud and Office365.
We keep your systems monitored and running around-the-clock for a fixed monthly fee. With us acting as your IT department, you can focus on your business, while we take care of your total IT system.
Protect your entire network infrastructure by adding a comprehensive security solution, including blocking unauthorized access, providing a strong first line of defence against viruses and malware, blocking spam emails
Actively Managed Routers
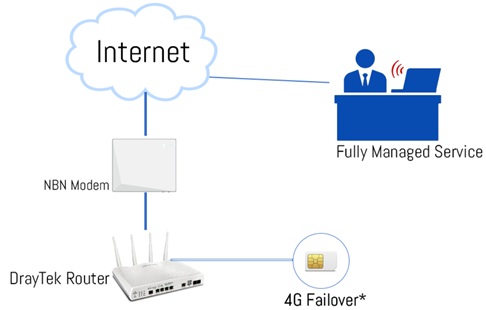
An enterprise grade router is the building block of connectivity and managing it requires expertise to ensure minimal disruptions.
With out managed router service, EvotecIT will be notified of any faults that may occur during business hours, giving you an enterprise grade solution without having to put time and money into training and hardware.
We provide end-to-end management of your Draytek router. Giving you comprehensive visibility of your NBN data through enhanced network and application reporting, freeing up IT staff to focus on business applications, rather than running the WAN.
- Network monitoring and fault identification
- Fault resolution
- Ongoing configuration management
- Reports
As networks become more complex, technology has evolved to become far more sophisticated and carry out several important tasks that keep communication flowing efficiently and securely.
- Network continuity
- Minimise disruption
- Router support
- Timely maintenance
- Hardware replacement support
Security Endpoint Servers
Endpoint security is the process of securing the various endpoints on a network. Any device, such as a smartphone, tablet or laptop, provides an entry point for threats. Adequately secure every endpoint connecting to a network to block access attempts and other risky activity at these points of entry.
The need for effective endpoint security measures has increased substantially, particular in light of the rise in mobile threats. A centralised security solution is no longer effective as more employees are relying on mobile devices and home computers to connect to the companies network.
By requiring endpoint devices meet security standards prior to network access, your business can maintain greater control over the ever-growing number of access points and threats.

Endpoint security products ,ay contain features and functionality such as;
- Data loss prevention
- Insider threat protection
- Disk, endpoint, and email encryption
- Application white-listening or control
- Network access control
- Data classification
- Endpoint detection and response
- Privileged user control
The process of protecting the network from unwanted users, attacks and intrusions.
Apps require constant updates and testing to ensure these programs are secure from attacks.
Remote access is a necessary part of business, but can also be a weak point for data. Endpoint security is the process of protecting remote access to a company’s network.
Inside of networks and applications is data. Protecting company and customer information is a separate layer of security
Essentially, this is a process of understanding the access every individual has in an organization.
Everything in a network involves databases and physical equipment. Protecting these devices is equally important.
Many files are in digital environments or “the cloud”. Protecting data in a 100% online environment presents a large amount of challenges.
Mobile phones and tablets involve virtually every type of security challenge in and of themselves.
In the event of a breach, natural disaster or other event data must be protected and business must go on. For this, you’ll need a plan. End-user education: Users may be employees accessing the network or customers logging on to a company app. Educating good habits (password changes, 2-factor authentication, etc.) is an important part of cybersecurity.
Cyber Security
Computer security, cybersecurity or information technology security is the protection of computer systems and networks from information disclosure, theft of or damage to their hardware, software, or electronic data, as well as from the disruption or misdirection of the services they provide.